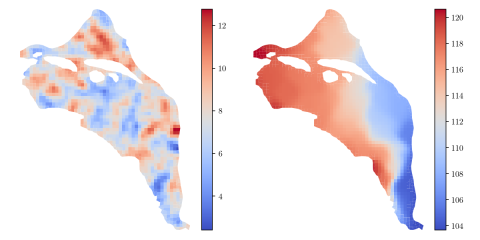
Exhaled breath condensate proteomics represent a low-cost, non-invasive alternative for examining upper respiratory health. EBC has previously been used for the discovery and validation of detected exhaled volatiles and non-volatile biomarkers of disease related to upper respiratory system distress...
Filter results
Category
- (-) National Security (21)
- (-) Plant Science (3)
- Scientific Discovery (307)
- Biology (198)
- Earth System Science (136)
- Human Health (102)
- Integrative Omics (73)
- Microbiome Science (42)
- Computational Research (23)
- Computing & Analytics (14)
- Chemistry (10)
- Energy Resiliency (9)
- Data Analytics & Machine Learning (8)
- Materials Science (7)
- Visual Analytics (6)
- Chemical & Biological Signatures Science (5)
- Computational Mathematics & Statistics (5)
- Weapons of Mass Effect (5)
- Atmospheric Science (4)
- Coastal Science (4)
- Ecosystem Science (4)
- Renewable Energy (4)
- Data Analytics & Machine Learning (3)
- Cybersecurity (2)
- Distribution (2)
- Electric Grid Modernization (2)
- Energy Efficiency (2)
- Energy Storage (2)
- Grid Cybersecurity (2)
- Solar Energy (2)
- Bioenergy Technologies (1)
- Computational Mathematics & Statistics (1)
- Grid Analytics (1)
- High-Performance Computing (1)
- Subsurface Science (1)
- Terrestrial Aquatics (1)
- Transportation (1)
- Wind Energy (1)
Content type
Tags
- Synthetic (5)
- Cybersecurity (2)
- Electrical energy (2)
- Omics (2)
- Proteomics (2)
- Bacterial Persistence (1)
- Bacterial Signaling (1)
- Bioenergy Production (1)
- Data inventory (1)
- Droughts (1)
- EBC (1)
- Exhaled Breath Condensate (1)
- Extreme weather (1)
- Fires (1)
- Heatwaves (1)
- High-Performance Computing (1)
- Imaging (1)
- Machine Learning (1)
- Mass Spectrometry (1)
- Metabolic Networks (1)
- ML/AI (1)
- PerCon SFA (1)
- Predictive Modeling (1)
- Quantification (1)
- Spectroscopy (1)
- TMT (1)
- Tomography (1)
"Visualizing the Hidden Half: Plant-Microbe Interactions in the Rhizosphere" Plant roots and the associated rhizosphere constitute a dynamic environment that fosters numerous intra- and interkingdom interactions, including metabolite exchange between plants and soil mediated by root exudates and the...
HDF5 file containing 10,000 hydraulic transmissivity inputs and the corresponding hydraulic pressure field outputs for a two-dimensional saturated flow model of the Hanford Site. The inputs are generated by sampling a 1,000-dimensional Kosambi-Karhunen-Loève (KKL) model of the transmissivity field...
This data is a model of synthetic adversarial activity surrounded by noise and was funded by DARPA. The various versions include gradually more complex networks of activities.
Category
Datasets
1
Category
Datasets
7
Category
Datasets
1
This data is a model of synthetic adversarial activity surrounded by noise and was funded by DARPA. The various versions include gradually more complex networks of activities.
Category
Datasets
1
Datasets
1
Short Biography Caroline (Carrie) Harwood received her Ph.D. in microbiology from the University of Massachusetts and completed postdoctoral work at Yale University. She held academic appointments at Cornell University and the University of Iowa before moving to the University of Washington in 2005...
Category
This data was generated by the organization IvySys. Activities can be phone calls, transactions, or any other type of communications. Most of the files are of the type .edges, .rdf, or .csv; but all can be opened in a text editor. A good introduction to this data can be found in \Tutorial1\MAA...
Category
Dataset The dataset will consist of: About 1200 news stories from the Alderwood Daily News plus a few other items collected by the previous investigators A few photos A few maps of Alderwood and vicinity (in bitmap image form) A few files with other mixed materials, e.g. a spreadsheet with voter...
Category
It is Fall of 2004 and one of your analyst colleagues has been called away from her current tasks to an emergency. The boss has given you the assignment of picking up her investigation and completing her task. She has been asked to pursue a line of investigation into some unexpected activities...
Category
Mini Challenge 1: Wiki Editors The Paraiso movement is controversial and is having considerable social impact in a specific area of the world. We have extracted a segment of the Paraiso (the movement) Wikipedia edits page. Please note this is not the Paraiso Manifesto Wiki page which is part of the...
Category
The VAST 2009 Challenge scenario concerned a fictitious, cyber security event. An employee leaked important information from an embassy to a criminal organization. Participants were asked to discover the identity ofthe employee and the structure of the criminal organization. Participants were...