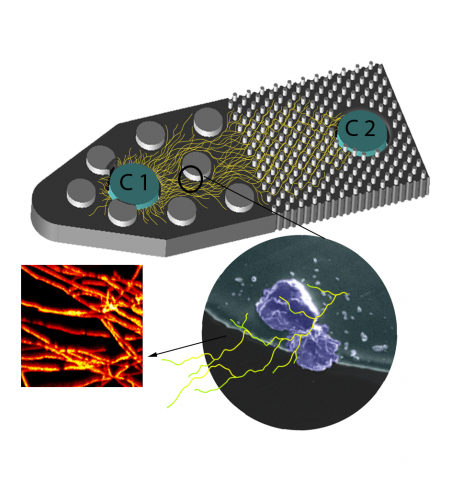
David Degnan is a biological data scientist who develops bioinformatic and statistical pipelines for multi-omics data, specifically the fields of proteomics, metabolomics, and multi-omics (phenotypic) data integration. He has experience with top-down & bottom-up proteomics analysis, genomics &...
Filter results
Category
- (-) Energy Resiliency (9)
- (-) Visual Analytics (6)
- (-) Computational Mathematics & Statistics (5)
- Scientific Discovery (307)
- Biology (198)
- Earth System Science (136)
- Human Health (102)
- Integrative Omics (73)
- Microbiome Science (42)
- Computational Research (23)
- National Security (21)
- Computing & Analytics (14)
- Chemistry (10)
- Data Analytics & Machine Learning (8)
- Materials Science (7)
- Chemical & Biological Signatures Science (5)
- Weapons of Mass Effect (5)
- Atmospheric Science (4)
- Coastal Science (4)
- Ecosystem Science (4)
- Renewable Energy (4)
- Data Analytics & Machine Learning (3)
- Plant Science (3)
- Cybersecurity (2)
- Distribution (2)
- Electric Grid Modernization (2)
- Energy Efficiency (2)
- Energy Storage (2)
- Grid Cybersecurity (2)
- Solar Energy (2)
- Bioenergy Technologies (1)
- Computational Mathematics & Statistics (1)
- Grid Analytics (1)
- High-Performance Computing (1)
- Subsurface Science (1)
- Terrestrial Aquatics (1)
- Transportation (1)
- Wind Energy (1)
Content type
Tags
- Cybersecurity (2)
- Electrical energy (2)
- Energy Equity (2)
- Energy Storage (2)
- Autoimmunity (1)
- Data Analysis (1)
- Energy Burden (1)
- Energy Justice (1)
- Heat Exchanger (1)
- Hydrothermal Liquefaction (1)
- Machine Learning (1)
- Output Databases (1)
- Renewable Energy (1)
- Solar photovoltaics (1)
- Type 1 Diabetes (1)
- Weatherization (1)
- Wet Waste (1)
Fusarium sp. DS682 Proteogenomics Statistical Data Analysis of SFA dataset download: 10.25584/KSOmicsFspDS682/1766303 . GitHub Repository Source: https://github.com/lmbramer/Fusarium-sp.-DS-682-Proteogenomics MaxQuant Export Files (txt) Trelliscope Boxplots (jsonp) Fusarium Report (.Rmd, html)...
Comprised of 6,426 sample runs, The Environmental Determinants of Diabetes in the Young (TEDDY) proteomics validation study constitutes one of the largest targeted proteomics studies in the literature to date. Making quality control (QC) and donor sample data available to researchers aligns with...
Federal and state decarbonization goals have led to numerous financial incentives and policies designed to increase access and adoption of renewable energy systems. In combination with the declining cost of both solar photovoltaic and battery energy storage systems and rising electric utility rates...
Category
PNNL’s Vision Statement for Equity in the Power Grid Drawing from a wealth of interdisciplinary research in grid modernization, PNNL is spearheading an effort to advance equity and energy justice through the role of scientific research with the goal of building an advanced national power grid...
Datasets
2
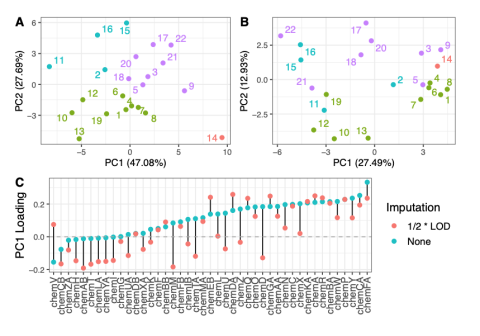
This data is supplementary to the manuscript Expanding the access of wearable silicone wristbands in community-engaged research through best practices in data analysis and integration by Lisa M. Bramer, Holly M. Dixon, David J. Degnan, Diana Rohlman, Julie B. Herbstman, Kim A. Anderson, and Katrina...
As energy prices rise and climate change brings more extreme and frequent days of heating and cooling, households must allocate more of their income to energy bills, increasing their energy burden. Many strategies are employed to alleviate high energy burden, such as weatherization, energy...
Category
A total of 172 children from the DAISY study with multiple plasma samples collected over time, with up to 23 years of follow-up, were characterized via proteomics analysis. Of the children there were 40 controls and 132 cases. All 132 cases had measurements across time relative to IA. Sampling was...
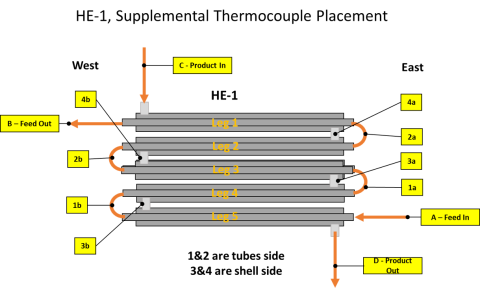
The presentation and supporting information provide data on the performance of an engineering-scale cross-flow heat exchanger used in hydrothermal liquefaction (HTL). Temperature profiles are provide for the process of waste water treatment sludges and a food waste. The data can be used to model...
Category
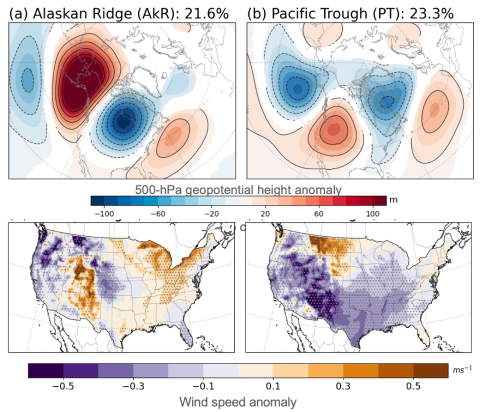
Supporting data and code uploaded to DataHub for "How do the weather regimes drive wind speed and power production at the sub-seasonal to seasonal timescales over the CONUS?" Created by Ye Liu*, Sha Feng*, Yun Qian, Berg K Larry, Huilin Huang *POC: Ye Liu, Ye.Liu@pnnl.gov Sha Feng, sfeng@pnnl.gov --...
Category
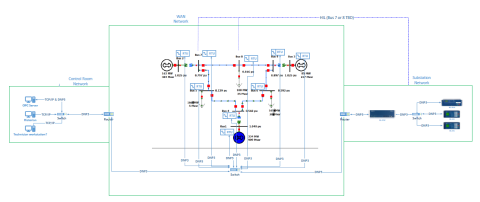
This dataset includes one baseline and three cybersecurity based scenarios utilizing the IEEE 9 Bus Model. This instantiation of the IEEE 9 model was built utilizing the OpalRT Simulator ePhasorsim module, with Bus 7 represented by hardware in the loop (HiL). The HiL was represented by two SEL351s...
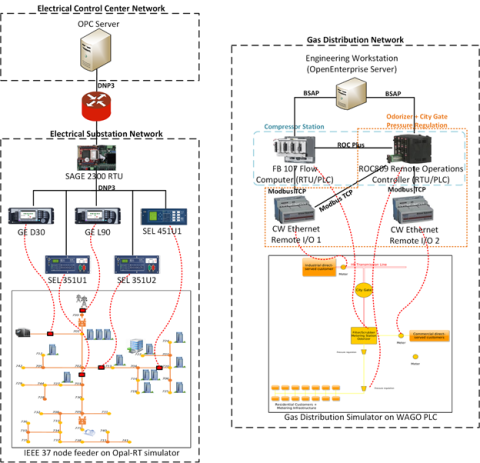
This dataset includes the results of high-fidelity, hardware in the loop experimentation on simulated models of representative electric and natural gas distribution systems with real cyber attack test cases. Such datasets are extremely important not only in understanding the system behavior during...
This year’s VAST Challenge focuses on visual analytics applications for both large scale situation analysis and cyber security. We have two mini-challenges to test your analytical skills and confound your visual analytics applications. In the first mini-challenge, (the imaginary) BankWorld's largest...
Category
The VAST 2010 Challenge consisted of three mini-challenges (MC) and one Grand Challenge (GC). Each MC had a data set, instructions and a number of questions to be answered. The GC required participants to pull together information from all three data sets and write a debrief summarizing the...
Category
The VAST 2009 Challenge scenario concerned a fictitious, cyber security event. An employee leaked important information from an embassy to a criminal organization. Participants were asked to discover the identity ofthe employee and the structure of the criminal organization. Participants were...