Description
This dataset includes the results of high-fidelity, hardware in the loop experimentation on simulated models of representative electric and natural gas distribution systems with real cyber attack test cases. Such datasets are extremely important not only in understanding the system behavior during various attack test cases, but also in evaluating novel intrusion detection approaches.
The dataset specifically includes the following scenarios, which were created for both the electrical and gas distribution systems as appropriate:
1. Normal traffic - This test case was to establish the baseline operation of the devices in the test environment.
2. System fault events - In the electrical system, we created a fault at a specific location on the microgrid system running in the OPAL-RT simulator. Similarly, in the gas system, this test created measurements corresponding to a faulted case on the gas distribution simulator.
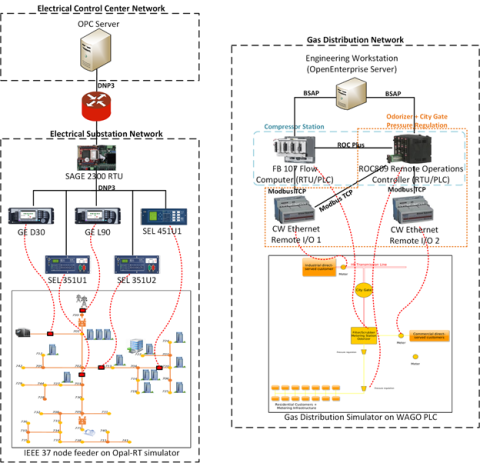
3. Connecting from an unauthorized IP address - This test case was to connect to specific devices on the electrical (SAGE RTU, an SEL 451 relay, and a GE D30) and the gas networks (ROC 800 and Flo Boss) using an unauthorized IP address.
4. Sending a malformed packet (bad CRC) - This test case was to send malformed DNP3 packets with bad CRCs on the electrical system to the SAGE RTU and SEL 451.
5. Identity spoofing - This test case involved spoofing the identity of the SCADA master (OPC and Open Enterprise servers) to interact with the field devices (SAGE 2300 and ROC 800).
6. Fuzz testing - This test case involved the use of protocol fuzzing libraries on field devices. DNP3 packets targeting the SAGE RTU, SEL 451 and Modbus packets targeting the ROC
809, FloBoss, and the Control Wave Remote IOs.
7. Handling risky/low-likelihood commands - This test case involved sending risky and low likelihood DNP3 commands such as cold restart, disabling unsolicited messages, file transfers, etc., to the SAGE RTU.
8. Man-in-the-Middle (MitM) with ARP spoofing - This test case involved a ARP based MiTM attack on the values sent from the SAGE RTU to the OPC server: (1) blocking commands sent to the RTU, (2) blocking measurements reported by the RTU, (3) injecting commands to the RTU, and (4) modifying measurements being sent from the RTU.
9. Reconnaissance (Poll all IPs/slave addresses with integrity poll) - This test case involved a scenario where an attacker performs reconnaissance by: 1) performing integrity polls on the subnet with targeted DNP3 slave addresses, 2) performing integrity polls on the subnet with a sweep of all possible DNP3 slave
addresses.
10. Reconnaissance (Device attributes scan) - This test case involved a scenario where an attacker performs reconnaissance by polling all devices on a network using a DNP3 device attributes scan (object 0 with a few variations) and a Modbus packet with function code 43 / 14 (0x2B / 0x0E) .
11. Data Injection - This test case involved sending a DNP3 binary output command to the SAGE RTU and a Modbus write command to the FloBoss RTU.
12. Configuration management - This test case involved interacting with the field devices using the respective vendor
software to perform configuration management.
13. Handling TCP behavior - This test case covered two types of scenarios: (1) cases where the TCP payload consists of multiple SCADA application payloads assembled together, (2) cases where a single SCADA application payload is arbitrarily split across multiple TCP packets.
14. Handling various protocol function codes - This test case involved interacting with the target devices by systematically sending various types of DNP3 and Modbus function codes with different options.