Biomedical Resilience & Readiness in Adverse Operating Environments (BRAVE) Project: Exhaled Breath Condensate (EBC) TMT Proteomic Transformation Data Exhaled breath condensate (EBC) represents a low-cost and non-invasive means of examining respiratory health. EBC has been used to discover and...
Filter results
Category
- (-) National Security (31)
- (-) Computational Mathematics & Statistics (7)
- Scientific Discovery (369)
- Biology (258)
- Earth System Science (161)
- Human Health (112)
- Integrative Omics (73)
- Microbiome Science (47)
- Computational Research (25)
- Computing & Analytics (17)
- Chemical & Biological Signatures Science (12)
- Energy Resiliency (12)
- Weapons of Mass Effect (12)
- Chemistry (10)
- Data Analytics & Machine Learning (9)
- Materials Science (7)
- Atmospheric Science (6)
- Data Analytics & Machine Learning (6)
- Renewable Energy (6)
- Visual Analytics (6)
- Coastal Science (4)
- Ecosystem Science (4)
- Energy Storage (3)
- Plant Science (3)
- Solar Energy (3)
- Bioenergy Technologies (2)
- Cybersecurity (2)
- Distribution (2)
- Electric Grid Modernization (2)
- Energy Efficiency (2)
- Grid Cybersecurity (2)
- Transportation (2)
- Computational Mathematics & Statistics (1)
- Grid Analytics (1)
- High-Performance Computing (1)
- Subsurface Science (1)
- Terrestrial Aquatics (1)
- Wind Energy (1)
Content type
Tags
- Predictive Phenomics (6)
- Proteomics (6)
- Synthetic (5)
- TA1 (5)
- TA2 (5)
- Homo sapiens (4)
- Mass Spectrometry (4)
- HCoV-299E (3)
- Limited Proteolysis (3)
- Biological Systems (2)
- Cybersecurity (2)
- Electrical energy (2)
- Global Analysis (2)
- Label-Free Quantitation (2)
- Machine Learning (2)
- Multi-Omics (2)
- Proteome Integral Solubility Alteration (2)
- S. elongatus PCC 7942 (2)
- Tandem Mass Tag (2)
- Carbon Cycling (1)
- Data Analysis (1)
- EBC (1)
- Exhaled Breath Condensate (1)
- High-Performance Computing (1)
- High Throughput Sequencing (1)
- Host Response (1)
- Omics (1)
- Output Databases (1)
- Quantification (1)
- TMT (1)
This year’s VAST Challenge focuses on visual analytics applications for both large scale situation analysis and cyber security. We have two mini-challenges to test your analytical skills and confound your visual analytics applications. In the first mini-challenge, (the imaginary) BankWorld's largest...
Category
The VAST 2010 Challenge consisted of three mini-challenges (MC) and one Grand Challenge (GC). Each MC had a data set, instructions and a number of questions to be answered. The GC required participants to pull together information from all three data sets and write a debrief summarizing the...
Category
The VAST 2009 Challenge scenario concerned a fictitious, cyber security event. An employee leaked important information from an embassy to a criminal organization. Participants were asked to discover the identity ofthe employee and the structure of the criminal organization. Participants were...
Category
Mini Challenge 1: Wiki Editors The Paraiso movement is controversial and is having considerable social impact in a specific area of the world. We have extracted a segment of the Paraiso (the movement) Wikipedia edits page. Please note this is not the Paraiso Manifesto Wiki page which is part of the...
Category
It is Fall of 2004 and one of your analyst colleagues has been called away from her current tasks to an emergency. The boss has given you the assignment of picking up her investigation and completing her task. She has been asked to pursue a line of investigation into some unexpected activities...
Category
Dataset The dataset will consist of: About 1200 news stories from the Alderwood Daily News plus a few other items collected by the previous investigators A few photos A few maps of Alderwood and vicinity (in bitmap image form) A few files with other mixed materials, e.g. a spreadsheet with voter...
Category
This data was generated by the organization IvySys. Activities can be phone calls, transactions, or any other type of communications. Most of the files are of the type .edges, .rdf, or .csv; but all can be opened in a text editor. A good introduction to this data can be found in \Tutorial1\MAA...
Category
A template to document AI prompts. There are four files associated with this DOI. There is a version of the template with and without examples. There is a PDF and Word copy of both versions. Please cite as: Sheridan, S. 2025. "AI Prompt Documentation Template." https://doi.org/10.17605/OSF.IO/K7FUZ...
Category
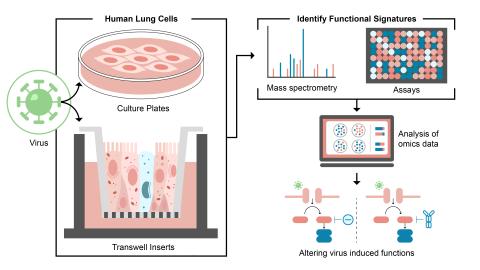
The research goal of this project is to identify and control host functions hijacked during viral infection through use of PNNL ‘omics technologies and modeling capabilities.
Datasets
5
The Human Islet Research Network (HIRN) is a large consortia with many research projects focused on understanding how beta cells are lost in type 1 diabetics (T1D) with a goal of finding how to protect against or replace the loss of functional beta cells. The consortia has multiple branches of...
Category
Datasets
1
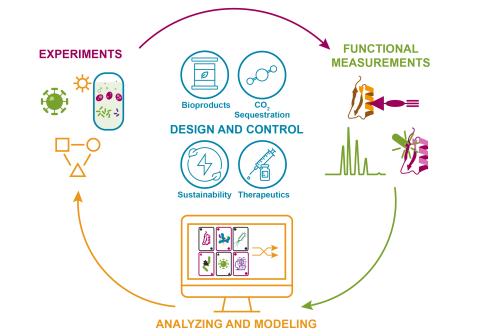
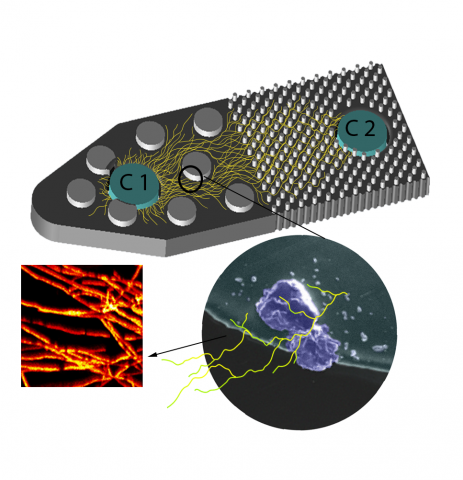
The Predictive Phenomics Science & Technology Initiative (PPI) at Pacific Northwest National Laboratory are tackling the grand challenge of understanding and predicting phenotype by identifying the molecular basis of function and enable function-driven design and control of biological systems...
Category
Datasets
17
David Degnan is a biological data scientist who develops bioinformatic and statistical pipelines for multi-omics data, specifically the fields of proteomics, metabolomics, and multi-omics (phenotypic) data integration. He has experience with top-down & bottom-up proteomics analysis, genomics &...
Fusarium sp. DS682 Proteogenomics Statistical Data Analysis of SFA dataset download: 10.25584/KSOmicsFspDS682/1766303 . GitHub Repository Source: https://github.com/lmbramer/Fusarium-sp.-DS-682-Proteogenomics MaxQuant Export Files (txt) Trelliscope Boxplots (jsonp) Fusarium Report (.Rmd, html)...
Datasets
1