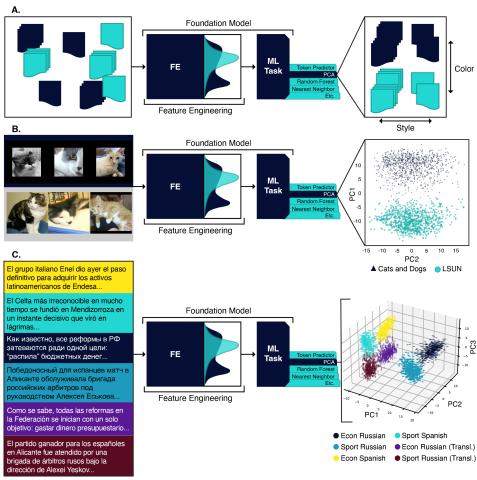
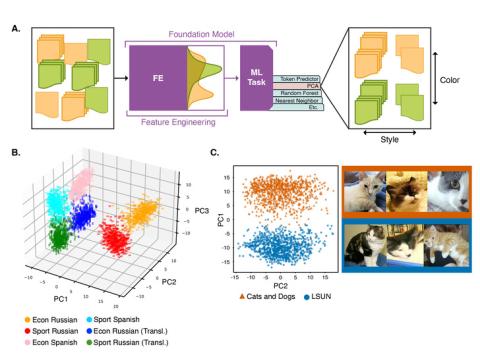
This repository contains data and code for the experiments run in the paper "Understanding Generative AI Content with Embedding Models" ( https://arxiv.org/abs/2408.10437 ). DataBase POC: Max Vargas (max.vargas@pnnl.gov) The data is separated by experiment: A. The `stack_exchange` dataset contains a...
Filter results
Category
- (-) Computing & Analytics (18)
- (-) Energy Resiliency (13)
- Scientific Discovery (379)
- Biology (263)
- Earth System Science (166)
- Human Health (112)
- Integrative Omics (74)
- Microbiome Science (50)
- National Security (32)
- Computational Research (25)
- Chemical & Biological Signatures Science (12)
- Weapons of Mass Effect (12)
- Materials Science (11)
- Chemistry (10)
- Data Analytics & Machine Learning (9)
- Computational Mathematics & Statistics (7)
- Data Analytics & Machine Learning (7)
- Renewable Energy (7)
- Atmospheric Science (6)
- Ecosystem Science (6)
- Visual Analytics (6)
- Coastal Science (4)
- Energy Storage (4)
- Plant Science (4)
- Solar Energy (4)
- Bioenergy Technologies (3)
- Energy Efficiency (3)
- Transportation (3)
- Cybersecurity (2)
- Distribution (2)
- Electric Grid Modernization (2)
- Grid Cybersecurity (2)
- Subsurface Science (2)
- Wind Energy (2)
- Advanced Lighting (1)
- Computational Mathematics & Statistics (1)
- Environmental Management (1)
- Federal Buildings (1)
- Geothermal Energy (1)
- Grid Analytics (1)
- Grid Energy Storage (1)
- High-Performance Computing (1)
- Terrestrial Aquatics (1)
- Vehicle Technologies (1)
- Waste Processing (1)
- Water Power (1)
Content type
Tags
- Synthetic (5)
- Energy Equity (3)
- Energy Storage (3)
- Cybersecurity (2)
- Electrical energy (2)
- Heat Exchanger (2)
- Hydrothermal Liquefaction (2)
- Biological Systems (1)
- Data inventory (1)
- Droughts (1)
- dynamic LCA (1)
- Energy Burden (1)
- Energy Justice (1)
- Extreme weather (1)
- Fires (1)
- Heatwaves (1)
- High-Performance Computing (1)
- HTL MHTLS (1)
- hydrothermal processing (1)
- Machine Learning (1)
- ML/AI (1)
- Multi-Omics (1)
- Phenomics (1)
- Predictive Modeling (1)
- Renewable Energy (1)
- Solar Energy (1)
- Solar photovoltaics (1)
- temperature (1)
- Weatherization (1)
- Wet Waste (1)
Energy insecurity affects most low-income households in the United States. Energy insecurity, which is characterized by a household’s inability to afford their energy needs, often leads to risky choices, causing other forms of insecurity including food and health. Although there are government...
Category
This repository contains data for the experiments run in the paper "Understanding Generative AI Content with Embedding Models" ( https://arxiv.org/abs/2408.10437 ). DataBase POC: Max Vargas (max.vargas@pnnl.gov) The data is separated by experiment: A. The `stack_exchange` dataset contains a...
Category
Please cite as : Schmidt A.J. 2023. MHTLS Cross-flow Heat Exchanger Temperature Performance Data. [Data Set] PNNL DataHub. 10.25584/2476481 The presentation and supporting information provide data on the performance of an engineering-scale cross-flow heat exchanger used in hydrothermal liquefaction...
Category
Federal and state decarbonization goals have led to numerous financial incentives and policies designed to increase access and adoption of renewable energy systems. In combination with the declining cost of both solar photovoltaic and battery energy storage systems and rising electric utility rates...
Category
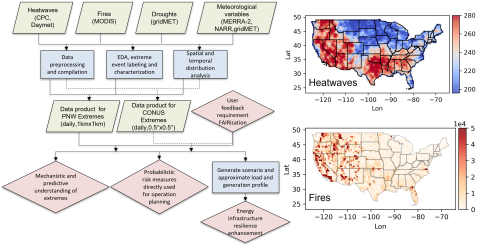
Extreme weather events, including fires, heatwaves(HWs), and droughts, have significant impacts on earth, environmental, and power energy systems. Mechanistic and predictive understanding, as well as probabilistic risk assessment of these extreme weather events, are crucial for detecting, planning...
As energy prices rise and climate change brings more extreme and frequent days of heating and cooling, households must allocate more of their income to energy bills, increasing their energy burden. Many strategies are employed to alleviate high energy burden, such as weatherization, energy...
Category
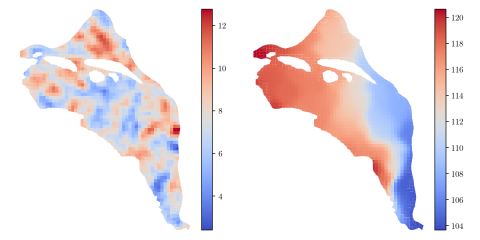
HDF5 file containing 10,000 hydraulic transmissivity inputs and the corresponding hydraulic pressure field outputs for a two-dimensional saturated flow model of the Hanford Site. The inputs are generated by sampling a 1,000-dimensional Kosambi-Karhunen-Loève (KKL) model of the transmissivity field...
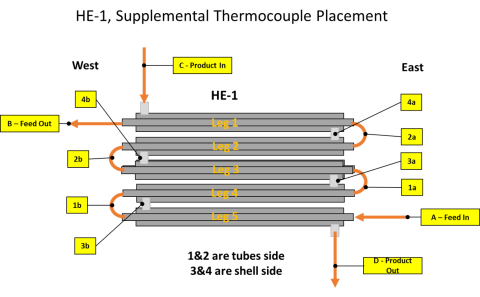
The presentation and supporting information provide data on the performance of an engineering-scale cross-flow heat exchanger used in hydrothermal liquefaction (HTL). Temperature profiles are provide for the process of waste water treatment sludges and a food waste. The data can be used to model...
Category
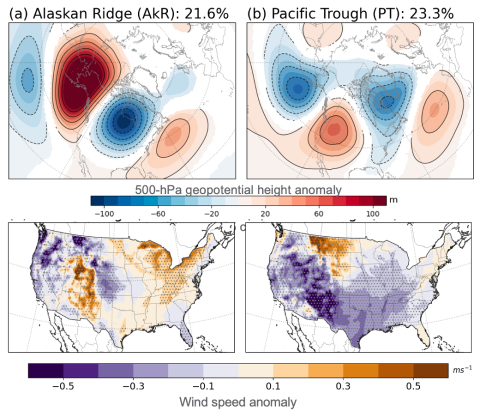
Supporting data and code uploaded to DataHub for "How do the weather regimes drive wind speed and power production at the sub-seasonal to seasonal timescales over the CONUS?" Created by Ye Liu*, Sha Feng*, Yun Qian, Berg K Larry, Huilin Huang *POC: Ye Liu, Ye.Liu@pnnl.gov Sha Feng, sfeng@pnnl.gov --...
Category
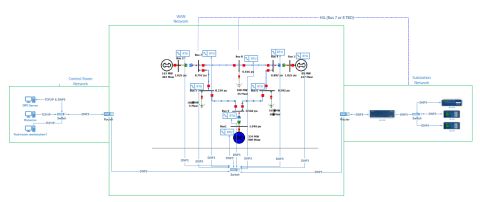
This dataset includes one baseline and three cybersecurity based scenarios utilizing the IEEE 9 Bus Model. This instantiation of the IEEE 9 model was built utilizing the OpalRT Simulator ePhasorsim module, with Bus 7 represented by hardware in the loop (HiL). The HiL was represented by two SEL351s...
ProxyTSPRD profiles are collected using NVIDIA Nsight Systems version 2020.3.2.6-87e152c and capture computational patterns from training deep learning-based time-series proxy-applications on four different levels: models (Long short-term Memory and Convolutional Neural Network), DL frameworks...
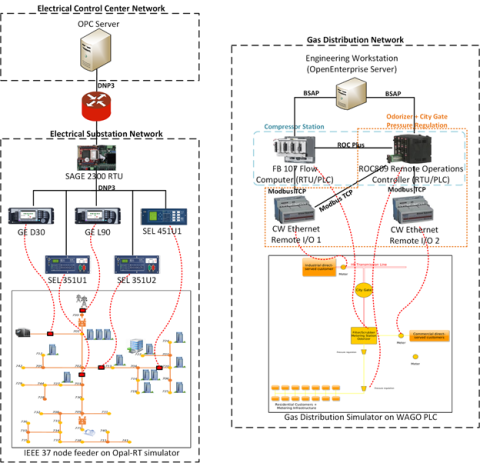
This dataset includes the results of high-fidelity, hardware in the loop experimentation on simulated models of representative electric and natural gas distribution systems with real cyber attack test cases. Such datasets are extremely important not only in understanding the system behavior during...
This year’s VAST Challenge focuses on visual analytics applications for both large scale situation analysis and cyber security. We have two mini-challenges to test your analytical skills and confound your visual analytics applications. In the first mini-challenge, (the imaginary) BankWorld's largest...
Category
The VAST 2010 Challenge consisted of three mini-challenges (MC) and one Grand Challenge (GC). Each MC had a data set, instructions and a number of questions to be answered. The GC required participants to pull together information from all three data sets and write a debrief summarizing the...