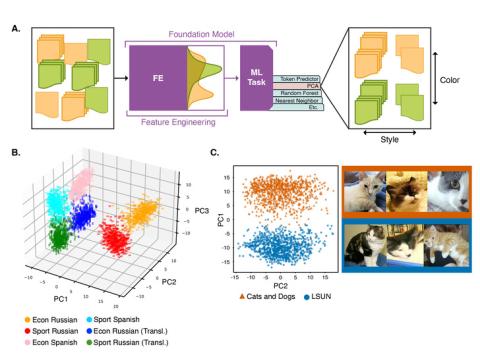
This repository contains data for the experiments run in the paper "Understanding Generative AI Content with Embedding Models" ( https://arxiv.org/abs/2408.10437 ). DataBase POC: Max Vargas (max.vargas@pnnl.gov) The data is separated by experiment: A. The `stack_exchange` dataset contains a...
Filter results
Category
- (-) National Security (31)
- Scientific Discovery (369)
- Biology (258)
- Earth System Science (161)
- Human Health (112)
- Integrative Omics (73)
- Microbiome Science (47)
- Computational Research (25)
- Computing & Analytics (17)
- Chemical & Biological Signatures Science (12)
- Energy Resiliency (12)
- Weapons of Mass Effect (12)
- Chemistry (10)
- Data Analytics & Machine Learning (9)
- Computational Mathematics & Statistics (7)
- Materials Science (7)
- Atmospheric Science (6)
- Data Analytics & Machine Learning (6)
- Renewable Energy (6)
- Visual Analytics (6)
- Coastal Science (4)
- Ecosystem Science (4)
- Energy Storage (3)
- Plant Science (3)
- Solar Energy (3)
- Bioenergy Technologies (2)
- Cybersecurity (2)
- Distribution (2)
- Electric Grid Modernization (2)
- Energy Efficiency (2)
- Grid Cybersecurity (2)
- Transportation (2)
- Computational Mathematics & Statistics (1)
- Grid Analytics (1)
- High-Performance Computing (1)
- Subsurface Science (1)
- Terrestrial Aquatics (1)
- Wind Energy (1)
Content type
Tags
- Predictive Phenomics (6)
- Proteomics (6)
- Synthetic (5)
- TA1 (5)
- TA2 (5)
- Homo sapiens (4)
- Mass Spectrometry (4)
- HCoV-299E (3)
- Limited Proteolysis (3)
- Cybersecurity (2)
- Electrical energy (2)
- Global Analysis (2)
- Label-Free Quantitation (2)
- Proteome Integral Solubility Alteration (2)
- S. elongatus PCC 7942 (2)
- Tandem Mass Tag (2)
- Carbon Cycling (1)
- EBC (1)
- Exhaled Breath Condensate (1)
- High-Performance Computing (1)
- High Throughput Sequencing (1)
- Host Response (1)
- Lethal Human Viruses (1)
- Machine Learning (1)
- Mass spectrometry data (1)
- Multi-Omics (1)
- Omics (1)
- PerCon SFA (1)
- Quantification (1)
- TMT (1)
Created on 2024-10-16T17:27:40+00:00 by LN Anderson . Pending updates will be available for public release before or by 2025-10-01.
Created on 2025-06-10T00:34:54+00:00 by LN Anderson
Created on 2024-10-16T17:27:40+00:00 by LN Anderson and is pending updates.
Created on 2024-10-16T17:27:40+00:00 by LN Anderson . Pending updates will be available for public release before or by 2025-10-01.
Created on updated 2024-10-01T21:34:23+00:00 by LN Anderson ; Last updated 2024-11-13T15:01:44+00:00 and is pending public release. Human Host Cellular Response to HCoV-229E Infection Proteomics (ACS-JM-DP2) The purpose of this experiment was to evaluate the human host cellular response to wild-type...
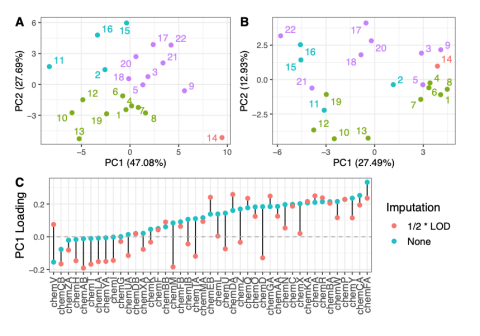
This data is supplementary to the manuscript Expanding the access of wearable silicone wristbands in community-engaged research through best practices in data analysis and integration by Lisa M. Bramer, Holly M. Dixon, David J. Degnan, Diana Rohlman, Julie B. Herbstman, Kim A. Anderson, and Katrina...
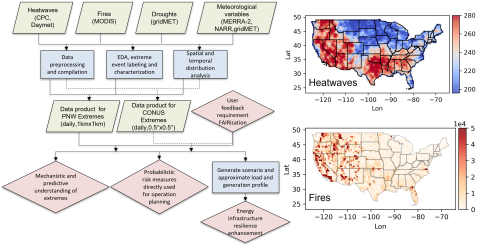
Extreme weather events, including fires, heatwaves(HWs), and droughts, have significant impacts on earth, environmental, and power energy systems. Mechanistic and predictive understanding, as well as probabilistic risk assessment of these extreme weather events, are crucial for detecting, planning...
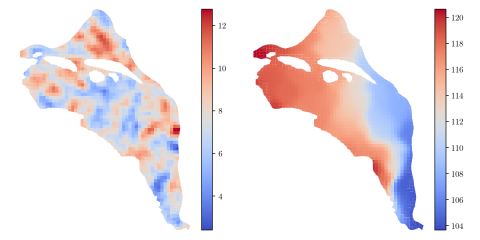
HDF5 file containing 10,000 hydraulic transmissivity inputs and the corresponding hydraulic pressure field outputs for a two-dimensional saturated flow model of the Hanford Site. The inputs are generated by sampling a 1,000-dimensional Kosambi-Karhunen-Loève (KKL) model of the transmissivity field...
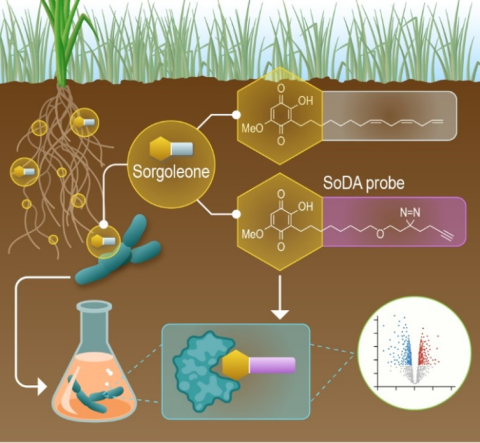
Last updated on 2024-09-17T15:49:08+00:00 by LN Anderson PerCon SFA: Profiling sorghum-microbe interactions with a specialized photoaffinity probe identifies key sorgoleone binders in Acinetobacter pitti Mass spectrometry-based global proteome analysis and SoDA-PAL photoaffinity probe labeled...
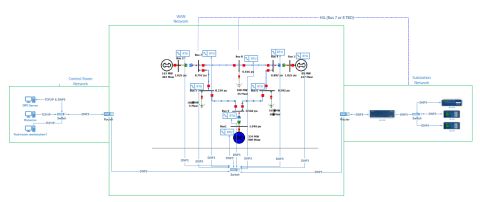
This dataset includes one baseline and three cybersecurity based scenarios utilizing the IEEE 9 Bus Model. This instantiation of the IEEE 9 model was built utilizing the OpalRT Simulator ePhasorsim module, with Bus 7 represented by hardware in the loop (HiL). The HiL was represented by two SEL351s...
ProxyTSPRD profiles are collected using NVIDIA Nsight Systems version 2020.3.2.6-87e152c and capture computational patterns from training deep learning-based time-series proxy-applications on four different levels: models (Long short-term Memory and Convolutional Neural Network), DL frameworks...
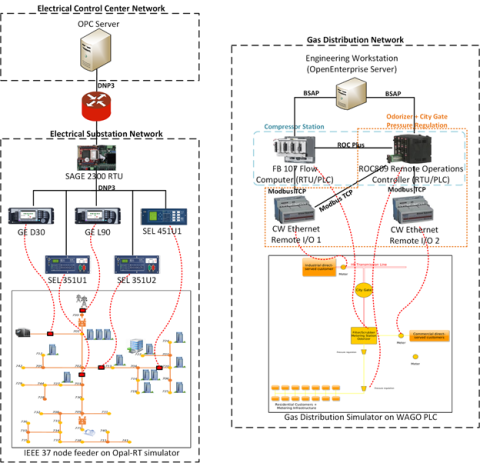
This dataset includes the results of high-fidelity, hardware in the loop experimentation on simulated models of representative electric and natural gas distribution systems with real cyber attack test cases. Such datasets are extremely important not only in understanding the system behavior during...
Biomedical Resilience & Readiness in Adverse Operating Environments (BRAVE) Project: Exhaled Breath Condensate (EBC) TMT Proteomic Transformation Data Exhaled breath condensate (EBC) represents a low-cost and non-invasive means of examining respiratory health. EBC has been used to discover and...
This year’s VAST Challenge focuses on visual analytics applications for both large scale situation analysis and cyber security. We have two mini-challenges to test your analytical skills and confound your visual analytics applications. In the first mini-challenge, (the imaginary) BankWorld's largest...